This post was originally published here
Introduction
SFTP (SSH File Transfer Protocol also known as Secure File Transfer Protocol) is a secure file transferring protocol between two remote systems, which runs over Secure Shell protocol (SSH). It provides strong authentication and secure encrypted data communication between two computers, which are connecting over an insecure network. It was designed by the Internet Engineering Task Force (IETF) as a secure extension. SSH provides the secure file transfer capabilities.
In this article, we will explain how to configure SFTP, how to use it with BizTalk Server and how you can set up monitoring SFTP using BizTalk360.
Contents
- How to Configure SFTP
- Types of authentication available in SFTP
- Using SFTP in BizTalk Server
- Monitoring SFTP using BizTalk360 Application
How to Configure SFTP
SFTP has replaced legacy FTP (File Transfer Protocol) and FTP/S and it provides all the functionality offered by these protocols, but the protocol is more secure and reliable. Also, configuration is easier.
Following are the steps to configure SFTP:
- Download the OpenSSH for server using OpenSSH for Windows binaries (Packages OpenSSH-Win64.zip or OpenSSH-Win32.zip)
Link: https://github.com/PowerShell/Win32-OpenSSH/releases
- Extract the package in folder location ‘C:Program Files’ as an administrator and install the SSH and SSHD services using the following command:
exe -Execution Policy Bypass -File install-sshd.psl - Once you have run the above command, the SSH server and server agent will install the system and start the service in the services.msc
The SFTP port number for the SSH port is 22, basically just an SSH Server. Once the user has logged in to the server using SSH, the SFTP protocol can be initiated. There is no separate SFTP port exposed on the servers. There is also no need to configure another rule into the firewalls.
Once the command is executed in PowerShell, the rule is created in the firewall section.
Using Public Keys for SSH Authentication
One effective way of securing SSH access to the server, is to use a Public/Private Key pair. This means that the generated key pair, consists of a public key (allowed to know) and a private key (keep secret and don’t give to anybody). The private key can generate a Signature and cannot be forged for anybody who doesn’t have that key. But using the public key, anybody can verify that a signature is genuine. The public key is placed on the server and a private key is placed on local workstation. Using a key pair, it becomes impossible for someone to log in by using just a password, in case you have set up SSH to deny password-based authentication.
Create the .ssh directory in a local folder and create a file named as “authorized_keys”, where we store the public key for authentication.
Generating Keys
PuTTYgen is a key generator. It generates pairs of public and private keys. When you run the PuTTYgen, you will see a window where you have two choices:
- Generate – to generate a new Public/Private key pair
- Load – to load an existing private key
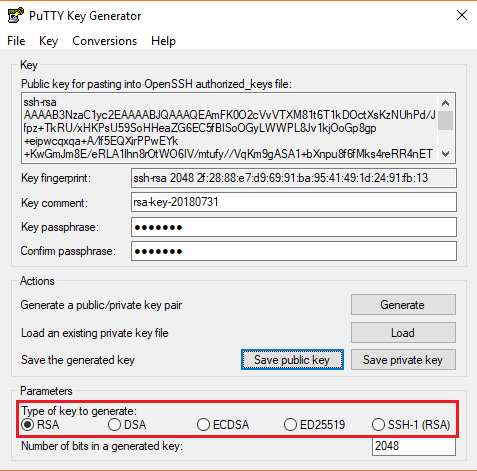
Before generating a key pair, using PuTTYgen, you need to select which type of key you need.
PuTTYgen currently supports the following type of keys:
- An RSA key for use with the SSH-1 protocol
- An RSA key for use with the SSH-2 protocol
- A DSA key for use with the SSH-2 protocol
- An ECDSA (Elliptic Curve DSA) key for use with the SSH-2 protocol
- An Ed25519 key (another elliptic curve algorithm) for use with the SSH-2 protocol
Here, we will generate a RSA key, for use with the SSH-1 Protocol.
- Download the PuTTYgen from the web site
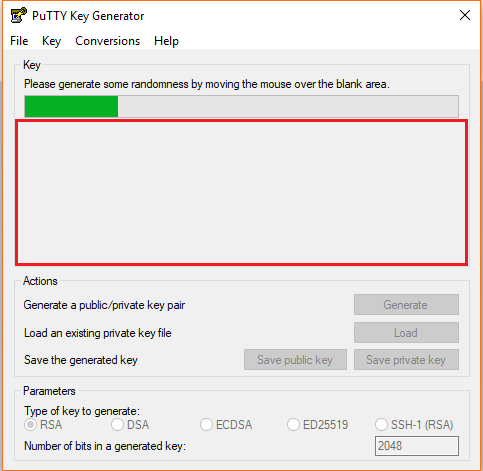
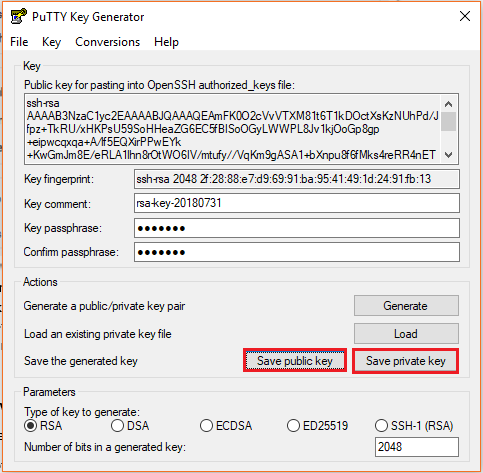
- Launch the program and click “Generate” button. The program generates the keys for you
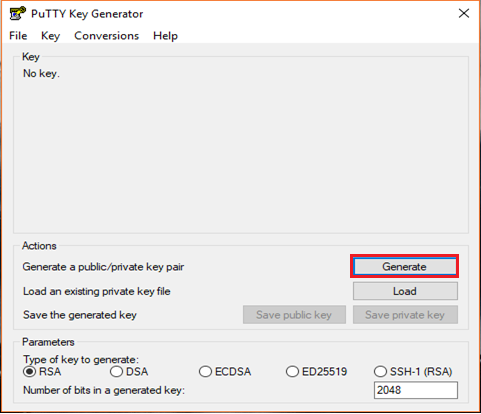
- Once you click the Generate button, you must generate some randomness, by moving the mouse over the blank area
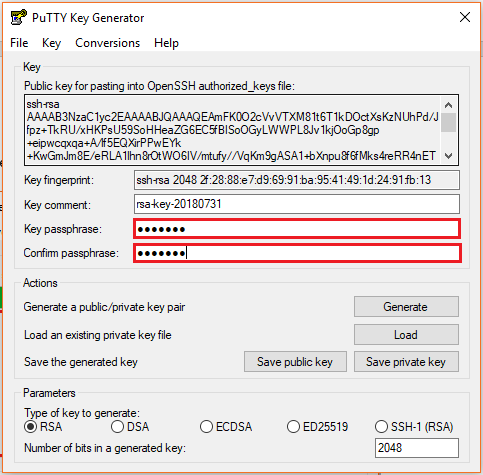
- Enter the unique Key passphrase and Confirm passphrase fields
- Save the public and private keys, by clicking Save Public Key and Save Private Key buttons
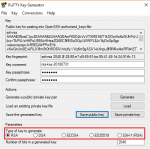
- From the Public Key, for pasting it into the OpenSSH authorized_keys file field at the top of the window, copy all the text (starting with ssh-rsa). The copied key must be pasted either into the public key tool, in the Control Panel, or directly into the authorized keys file on your server.
Using SFTP Adapter in BizTalk Server
BizTalk Server provides the SFTP adapter to send and receive a file from a secure FTP server using the SSH file transfer protocol. Let’s see how can configure the SFTP adapter for receiving and sending a file from the secure server.
- In the BizTalk Admin Console, create a SFTP Receive Port in the BizTalk application where you want to have it
- Create a Receive Location within that Receive Port
- Select the Transport Type as SFTP from the drop-down list
In the Properties section, configure the following steps:
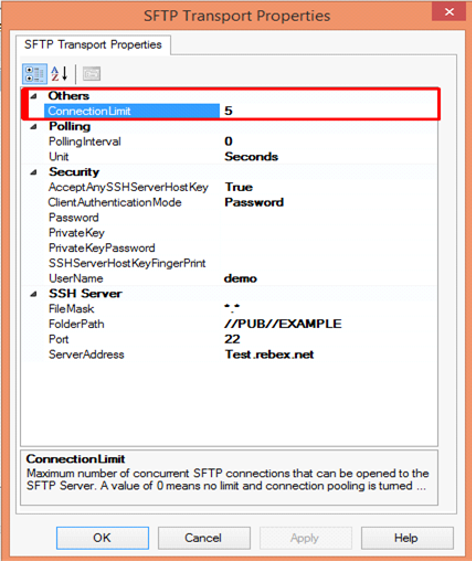
Others
- Connection Limit – Specify the maximum number of concurrent connections that can be opened to the server
Polling
- Polling Interval – Specify the interval at which the adapter polls the server. To poll continuously, set this value to zero
Default Value: 5
- Unit – Specifies the unit in which the polling interval is specified. For example: Seconds, Minutes, Hours or Days
Security
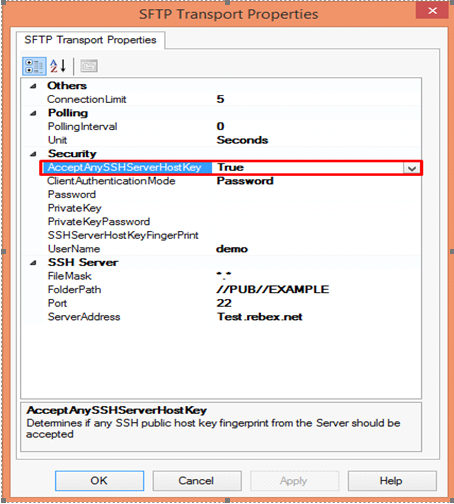
- Accept Any SSH Server Host key – When the option is set as True, SSH will accept the connection from the host server; when it is set as False, the Receive Location uses the fingerprint of the server for authentication. For the authentication, you need to provide the finger print in the SSHServerHostKeyFingerPrint field.
- Client Authentication
There are three client authentication methods:
- Password
- PublicKeyAuthentication
- MultiFactorAuthentication
Password authentication mode is simply providing the password in the console for authenticating the client. For the PublicKeyAuthentication, you must provide the private key file in the PrivateKey field and provide the passphrase in the PrivateKeyPassword for authenticating.
For MultiFactorAuthentication, the user must provide the user name, password and Privatekey. If the private key is protected by a passphrase, you also need to provide that in the privatekeyPassword field.
- Password – Specify the password, if you have set the ClientAuthentication mode to password
- Private Key – Specify the private key for the SFTP user, if you have set the ClientAuthenticationMode to Publickeyauthentication
- Private Key Password – Specify the passphrase key to validate the private key
- SSH Server Host Key Fingerprint – It specifies the fingerprint of the public host key for the SSH server
- Username – Specifies a username to log on to the SFTP server
SSH Server
- File Mask – Specifies the file mask to use when retrieving files from a secure SFTP server
- Folder path – Specifies the folder path on the secure SFTP server from where the Receive Location can retrieve files
- Port – Specifies the port address for the secure SFTP server on which the file transfer takes place
- Server Address – Specifies the server name or IP address of the secure SFTP server
Configuring the Send Port
For Configuring the Send Port, create a Send Port or double click an existing send port to modify it in an application in the BizTalk Administration Console.
- On the General Tab, Choose the type of SFTP artifact in the transport section and click the configuration button.
- In the SFTP Transport Properties window configure the following options based on requirement
Others
- Connection Limit – Maximum number of concurrent connections that can be opened to the server
- Log – Creating client-side log file to trouble shoot any errors. Enter the full path for creating the log file and its available from BizTalk Server 2016
- Temporary Folder – A temporary folder on the SFTP server to upload large files before automatically moved to the required location on the same server and its available from BizTalk server 2013 R2
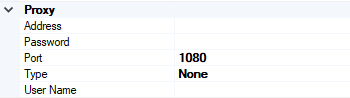
Proxy
- Address –Specifies either DNS or IP Address of the Proxy server
- Password –Specifies the Password of the proxy server
- Port – Specifies the port of the Proxy Server
- Type – Specifies the protocol used by the proxy server
- User Name – Specifies the User Name of the Proxy server
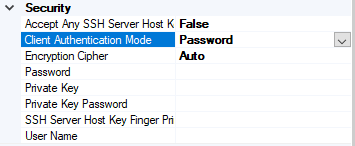
Security
- Access Any SSH Server Host Key – When True, the send port accept any SSH Public host key from the server and if set as false, the port matches the host key with the key specified in the SSHServerHostKey
- Client Authentication Mode – Specifies the authentication method that the send port uses for authenticating the client to the SSH Server.
Three modes of authentication
- Password – If set as Password , you must provide the password in the Password Property
- PublicKeyAuthentication – if set as PublicKeyAuthentication, you must provide the private key of the user in the PrivateKey
- MultiFactorAuthentication – if set as MultiFactorAuthentication, you must provide UserName with its Password. If the private key is protected by a password, provide the password in the PrivateKeyPassword as well
- EncryptionCipher – Provide the kind of encryption cipher and available from BizTalk Server 2013 R2. Options are Auto, AES and TripleDES in the BizTalk Server 2013 R2 and for the BizTalk Server 2016 Auto, AES, Arcfour, Blowfish, TripleDES, and
- Password – Specify the SFTP user password if you set the ClientAuthenticationMode to Password
- Private Key – Specify the private key for the SFTP user if you set the ClientAuthenticationMode to PublicKeyAuthentication
- Private Key Password – Specify a private key password, if required for the key specified in the PrivateKey
- SSH Server Host Key Finger Print – Specifies the fingerprint of the server used by the adapter to authenticate the server if the AccessAnySSHServerHostKey property is set to False. If the fingerprints do not match, the connection fails.
- User Name – Specifies the username for the secure FTP Server
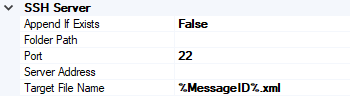
SSH Server
- Append If Exist – if the file being transferred to the secure FTP server already exists at the destination, this property specifies whether the data from the file being transferred should be appended to the existing file. If set to True, the data is appended. If set to False, the file at the destination server is overwritten
- Folder Path – Specifies the folder path on the secure FTP server where the file is copied
- Port – Specifies the port address for the secure FTP server on which the file transfer takes place
- Server Address – Specifies the server name or IP address of the secure FTP server
- Target File Name – Specifies the name with which the file is transferred to the secure FTP server. You can also use macros for the target file name
- Click Apply and OK again to save settings
Monitor the SFTP Location using BizTalk360
From the v8.4, under File Location in the Monitoring section, BizTalk360 has the capability to monitor SFTP servers. File Location Monitoring will list all the locations configured in the BizTalk artifacts (Send Ports and Receive Locations) for the SFTP Transport type. This helps users to easily monitor all the SFTP locations mapped within the Receive Locations/Send Ports.
It contains four sections:
- SSH Server Section has the details about the SFTP Location
- The Proxy Details Section is optional to connect to a SFTP Server behind a firewall
Note: In BizTalk, Proxy details are available from BizTalk 2013 R2
- Security Details Section has the authentication details
- In the SFTP Monitoring Config Section, you can configure the monitor with threshold conditions for the metric File Count
Based on the need, you can monitor the location with threshold conditions. If the specific condition is met, the user gets notified through an email, a SMS or another communication channel.
For monitoring the SFTP server, BizTalk360 uses the third-party tool nSoftware. Using the nSoftware IPWorks SSH product, BizTalk360 connects to the secure server with Private Keys and password for monitoring the location.
For monitoring the SFTP in BizTalk360 you can refer the knowledge base in this link.
See below, some code snippets for connecting to the secure server using nSoftware.
Password Authentication
sftp.SSHUser = “test”; sftp.SSHPassword = “password”; sftp.SSHPort = 22; sftp.SSHHost = “SSHHost”; sftp.Config(“SSHAcceptServerHostKeyFingerPrint=6a:d3:65:96:d1:9f:9d:f9:57:4e:6b:3b:11:57:5a:15”); sftp.SSHLogon(sftp.SSHHost, sftp.SSHPort); Console.WriteLine(“Authenticated”); sftp.SSHLogoff();
Public key Authentication
sftp.SSHUser = "test";
sftp.SSHCert = new Certificate(CertStoreTypes.cstPPKKeyFile, "....filesserver_cert.pem", "test", "*");
sftp.SSHAuthMode = SftpSSHAuthModes.amPublicKey;
sftp.SSHPort = 22;
sftp.SSHHost = "SSHHost";
sftp.Config("SSHAcceptServerHostKeyFingerPrint=6a:d3:65:96:d1:9f:9d:f9:57:4e:6b:3b:11:57:5a:15");
sftp.SSHLogon(sftp.SSHHost, sftp.SSHPort);
Console.WriteLine("Authenticated");
sftp.SSHLogoff()
Conclusion
This article demonstrates the creation of a SFTP Server. Using the SFTP server in BizTalk Receive Locations and Send Ports, you can send files securely and monitor the SFTP server using BizTalk360.
If you have any feedback or suggestions, please write to us at support@biztalk360.com.