This post was originally published here
Azure Application Gateway a Layer-7 HTTP load balancer that provides application-level routing and load balancing services. It distributes traffic requests based upon data found in application layer protocols such as HTTP/HTTPS and also on application specific data such as HTTP headers, cookies, or data within the application message itself, such as the value of a specific parameter.
You basically need to define rules to accept the traffic requests and route them to the appropriate back-end instances.
Application Gateway currently supports the following features:
- Web Application Firewall (WAF)
- Scaleble, highly-available HTTP load balancing solution
- Cookie-based session affinity
- SSL offload for better utilization
- URL-based content routing
- Multi-site routing
- Web socket support
- Health monitoring
- Advance diagnostics
While Azure is responsible for securing the infrastructure and platform that your application runs on, it is your responsibility to secure your application itself. Now Web Application Firewall (WAF) in Azure Application Gateway can provide protection to your web applications against common threats such as SQL injection, cross-site scripting attacks, and session hijacks.
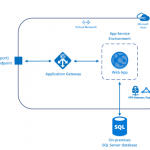
If your organization hosts highly sensitive information, the number-one priority is having a fully-isolated and dedicated environment for only your organization’s applications. Using an App Service Environment, your organization can have security and isolation for your web apps and use a virtual network for control over traffic.
An App Service Environment is a premium service plan option of Azure App Service that provides a fully isolated and dedicated environment. App Service Environments are isolated to run only a single customer’s applications and are always deployed into an Azure Virtual Network. At a high level, an App Service Environment consists of compute resources running in the Azure Hosted Service, Storage, Database, a Virtual Network, and a subnet with the hosted service running in it.
From a single open port, one option to block most traffic would be to use WAF in Application gateway in front of ASE to protect your Web apps.You can also Create a network security group, and assign it to a subnet in your Azure Virtual Network to restrict traffic to the App Service Environment from the WAF only by using the VIP address.
Here you have all the security with a straight forward architecture. Easy to provision, maintain and administer.
The path for request would be: App Gateway (WAF mode) –> ASE
To create this architecture here are the steps involved:
- Create a virtual network (ex: frontend-vnet) for both App Service Environment (ASE) and Application Gateway(AG).
- Create subnet for Application Gateway. Subnet for App Service Environment will be created as a part of ASE provision process.
- Creates an App Service Environment in your virtual network with a private internal load balancer address using Azure Quickstart Template. This step would take up to 2 hours to complete.
- Deploy a test web app – The vnet (frontend-vnet) is not publicly accessible so in order to deploy app, you need to create a Virtual Machine that is living within the same Virtual Network and use that to deploy and access the Web App with its internal IP. Once you have deployed your test web app, you should successfully be able to access it from any VM which is living within same vnet (frontend-vnet).
- Create WAF-enable Application Gateway
- Configure Application Gateway
- Test your web app form public endpoint.
In this blog post I will go through the creation and configuration of Application Gateway in detail.
Create WAF-enabled Application Gateway
In Azure Portal, Go to New—>Networking and select Application Gateway. Provide the information for the basic setting as shown below. Make sure you select WAF tier.
In the settings, make sure to select the same Virtual Network (frontend-vnet) you used to configure ASE earlier and the subnet you created specifically for the Application Gateway. You also need configure the public IP address.
Configure the WAF specific settings.
- Firewall status – This setting turns WAF on or off.
- Firewall mode – This setting determines the actions WAF takes on malicious traffic. If Detection is chosen, traffic is only logged. If Prevention is chosen, traffic is logged and stopped with a 403 Unauthorized.
Review the results and click on OK to create the gateway.
Configure the Application Gateway
Add servers to backend pool – Once the application gateway is created, go to the Backend Pools and select the current backend pool.
Add the IP address of ILB ASE and Save. Now the incoming traffic that enters the application gateway would be routed to the backend address added here.
Configure SSL offload – Application gateway can be configured to terminate the Secure Sockets Layer (SSL) session at the gateway to avoid costly task of decrypting HTTPS traffic off your web servers. Application gateway decrypts the request and sends it to backend server and re-encrypts the response before sending it back to the client.
To configure SSL offload with an application gateway, a certificate (pfx format) is required. This certificate is loaded on the application gateway and used to encrypt and decrypt the traffic sent via SSL.
Add an HTTPS listener – It will look for traffic based on its configuration and helps route the traffic to the backend pools. Click Listeners and click the Add button to add a listener. Fill out the required information for the listener and upload the .pfx certificate.
Create a rule and associate it to the listener – Once listener is created, you need to create a rule to handle the traffic from the listener. Click the Rules of the application gateway, and then click Add. Type in the friendly name for the rule and choose the listener created in the previous step. Choose the appropriate backend pool and http setting and click OK.
Create the custom probe – Custom probes allow you to have a more granular control over the health monitoring. When using custom probes, you can configure the probe interval, the URL and path to test, and how many failed responses to accept before marking the back-end pool instance as unhealthy.
Probes are configured in a two-step process through the portal. The first step is to create the probe. Next you add the probe to the backend http settings of the application gateway. Create a Custom Probe with the Host set as your custom Web App domain, for example sample-app.com as shown below.
Add probe to the gateway – Go to the HTTP settings, and make sure that the setting has Custom Probes turned on and select the probe you just created. Otherwise, the Application Gateway will try to go to the IP of the App Service Environment without passing a Host header, which won’t work and will throw the probe into an Unhealthy state resulting in the 502 Gateway Proxy error.
Testing
There are couple of ways to do the testing. First you can use ModHeader Chrome extension to open the public IP address/hostname of the Application Gateway in the browser. You need to pass in the Custom Domain you configured on the Web App as a Host Header and the website should come up. Refer Sabbour blog post for further detail.
The other way is to add hostname (sample-app.com) to Custom Domains in the setting of app deployed in ASE as shown below.
You need to add an entry for your host in Hosts file on your local machine. The path would be c:WindowsSystem32Driversetchosts.
Now if you go to https://sample-app.com it should open up the sample web app as shown below.
Logging and troubleshooting
Application Gateway provides following capabilities to monitor resources.
Backend health – Application gateway provides the capability to monitor the health of individual members of the backend pools through the portal, PowerShell, and CLI.
Logging – There are different types of logs in Azure to manage and troubleshoot application gateways such as performance, firewall and access logs.
Here is a sample firewall log.
There are three different options to choose for storing your logs
- Storage Account
- Event Hubs
- Log Analytics
Metrics – Application gateway currently has one metric. This metric measures the throughput of the application gateway in Bytes per second.
You can also set alert rule for application gateway based on metrics on a resource.
For example, an alert can email an administrator if the throughput of the application gateway is above, below or at a threshold for a specified period of time.
Summary
To summarize, we explored the option to protect your web applications against common threats such as SQL injection, cross-site scripting attacks, and session hijacks using Azure Application Gateway. We ‘ve hosted a Web App securely in an App Service Environment. This Web App isn’t publicly accessible as it is sitting in a subnet inside a Virtual Network and it isn’t exposed to the internet. The only way to access the site is through a Web Application Firewall enabled Application Gateway.